As tax season approaches, the importance of securing sensitive client information in cloud-hosted tax applications cannot be overstated. With increasing cyber threats, accounting firms and tax professionals must adopt robust cloud security measures to protect data integrity and client privacy. This blog outlines critical security concerns and best practices for hosting tax applications in the cloud, ensuring data protection and compliance with regulations while building trust with clients.
Understanding the Shared Responsibility Model
When utilizing cloud services, it’s essential to understand the shared responsibility model. In this framework, the cloud provider is responsible for the security of the cloud infrastructure, while users are responsible for securing their applications and data. Key questions to ask your cloud provider include:
- What security protocols do you have in place?
- How do you handle data breaches?
- Is data encrypted both in transit and at rest?
- What compliance standards do you meet?
By clarifying these responsibilities, businesses can better manage their security posture and ensure that they are not solely reliant on the provider’s security measures.
Identifying and Protecting Sensitive Data
Not all data is created equal; understanding which information is sensitive is crucial. Personally identifiable information (PII), such as social security numbers and financial details, requires stringent protection due to regulatory requirements. Implementing a data classification policy can help identify sensitive information and determine who has access to it. This policy should comply with federal, state, and local data privacy laws.
Implementing Strong Access Controls for Cloud Security
Access control measures are vital in minimizing unauthorized access to sensitive data. Here are some best practices:
- Robust Password Policies: Enforce complex passwords that include letters, numbers, and special characters. Regularly update passwords and prohibit reuse of old ones.
- Two-Factor Authentication (2FA): Require a second form of verification beyond just a password to enhance security.
- Role-Based Access Control (RBAC): Limit access based on user roles within the organization to ensure that employees only have access to the information necessary for their job functions.
10 Best Practices for Cloud Security and Data Protection
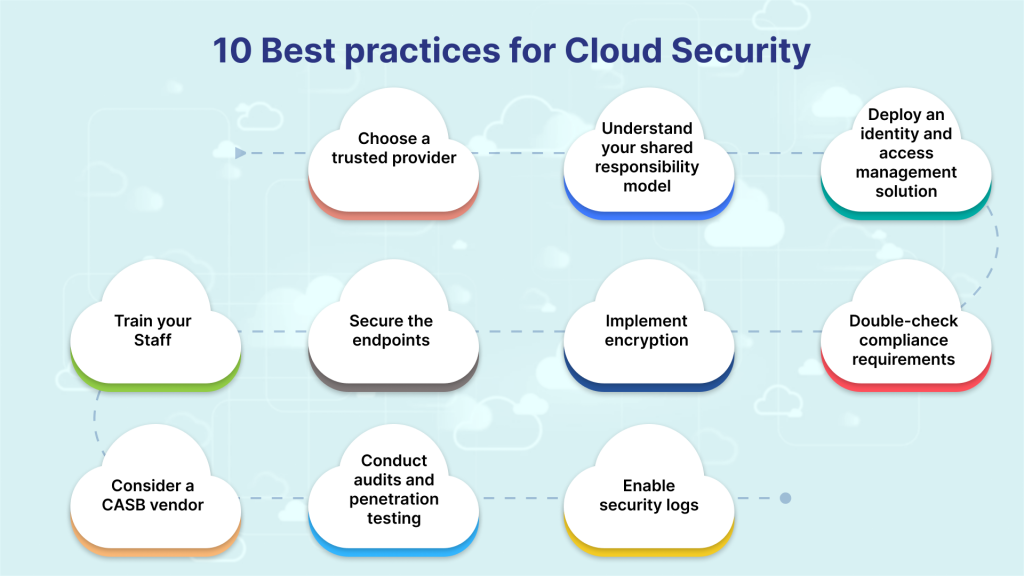
Regular Security Audits and Monitoring
Conducting regular security audits is essential for identifying vulnerabilities within your system. These audits should include:
- Internal Reviews: Regularly assess your security measures and update them as necessary.
- Third-Party Assessments: Engage external experts to conduct penetration testing and vulnerability assessments.
Continuous monitoring of systems can help detect suspicious activities early on, allowing for swift remediation of potential threats.
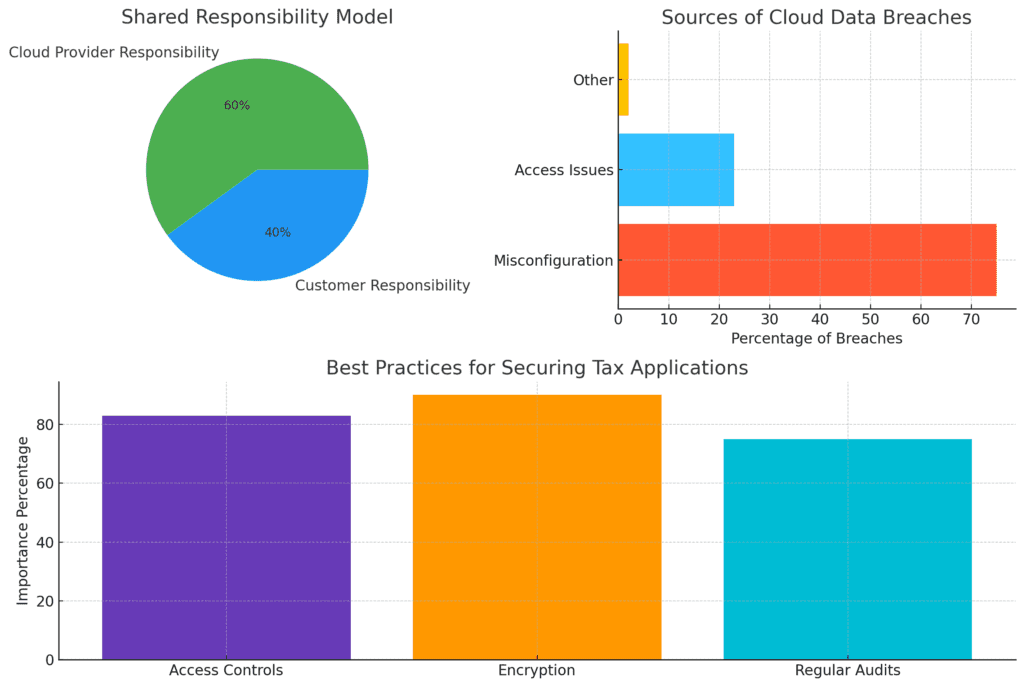
Data Encryption Practices
Encryption is a fundamental component of data security in the cloud. Implementing encryption protocols ensures that even if data is intercepted, it remains unreadable without the proper decryption keys.
- Encryption at Rest: Protect stored data using strong encryption algorithms.
- Encryption in Transit: Use TLS/SSL certificates to secure data as it travels between clients and servers.
Secure Backup Solutions
Regular backups are crucial for disaster recovery. Ensure that backups are:
- Encrypted: Protect backup data with encryption to prevent unauthorized access.
- Regularly Tested: Periodically test backup restoration processes to ensure that they work effectively when needed.
Compliance with Regulations
Compliance with regulations such as GDPR or HIPAA is non-negotiable when handling sensitive client information. Ensure that your cloud provider adheres to relevant compliance standards, which may include regular audits, data protection and certifications.
Conclusion
As tax applications increasingly migrate to the cloud, ensuring data and cloud security becomes paramount. By understanding the shared responsibility model, implementing strong access controls, conducting regular audits, encrypting data, and adhering to compliance regulations, businesses can protect sensitive client information effectively.
Connect with OneUp Networks today to securely host your tax and accounting applications.